Writing Reports
Contents
Writing Reports#
Cybersecurity is a critical field that demands meticulous attention to detail, especially when it comes to reporting on security incidents, assessments, or compliance. A well-crafted cybersecurity report not only communicates vital information to stakeholders but also serves as a tool for decision-making and strategy development. While the specifics of each report may vary depending on the context, certain foundational principles and guidelines are universally applicable. This article aims to provide a comprehensive overview of these general recommendations, offering a blueprint for creating effective and informative cybersecurity reports. Whether you are reporting on a data breach, system vulnerability, or compliance status, these guidelines will ensure your report is clear, concise, and actionable, catering to all types of cybersecurity reports.
Step 1 - Stakeholder Analysis#
A stakeholder is an individual, group, or organization that has an interest or concern in a particular project, business, or endeavor. Stakeholders are key to the success of a project as they can affect or be affected by the project’s outcomes. They can include employees, customers, investors, suppliers, communities, governments, or any entity impacted by the project or business activities. Stakeholders may have a direct or indirect influence on the project, offering insights, resources, or support, and in turn, may benefit from its successful completion. Understanding and managing stakeholder needs and expectations are crucial for the success and sustainability of any project or business.
In cybersecurity, common stakeholders include:
Cyber Crime Investigators
Cyber Defense Analysts
Executive Cyber Leaders
Forensics Analysts
Incident Responders
Information Security Managers
Security Architects
and many more
Identify the Stakeholders#
Before you begin writing any report, the first step is to identify all the stakeholders for that report. There are three categories of stakeholders:
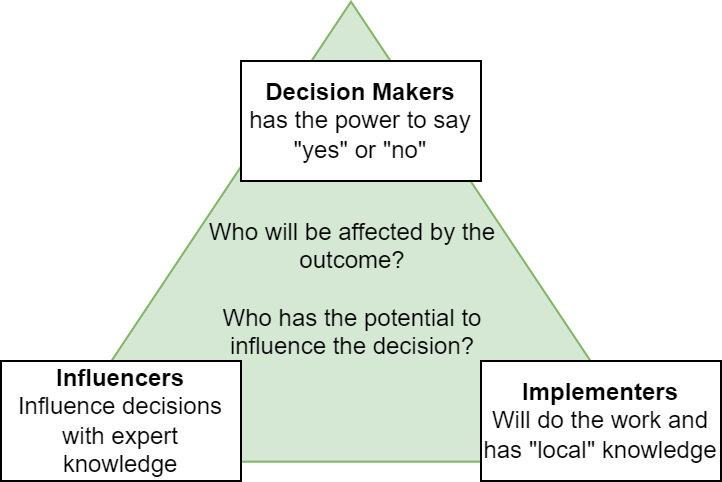
Decision Makers: These stakeholders are responsible for making the final decisions on cybersecurity initiatives, policies, and strategies. They may include top executives, such as the CEO, CIO, or CISO, as well as board members who have a direct impact on the direction of an organization’s cybersecurity program. Their primary role is to approve and support plans based on input from the other stakeholder groups.
Influencers: This group consists of individuals who can shape the decision-making process, even though they might not have the authority to make the final call. Influencers can be both internal and external to the organization. Internal influencers may include IT managers, cybersecurity team leads, or legal and compliance personnel, while external influencers might encompass industry experts, regulators, or even key customers. Their opinions, expertise, and guidance can significantly influence the decisions made by the Decision Makers.
Implementers: Implementers are responsible for putting cybersecurity plans and strategies into action. They play a crucial role in the day-to-day management and execution of cybersecurity initiatives. Implementers can include IT staff, cybersecurity professionals, system administrators, and even employees who follow security best practices in their daily tasks. Their hands-on experience and understanding of technical challenges can provide valuable insights to shape effective cybersecurity measures.
Map the needs and wants of stakeholders#
After determining who the report’s stakeholders are, you should analyze each one individually. This has to be completed in a standalone document.
A straightforward table used to determine the requirements stakeholders for a malware analysis report is shown in the image below:
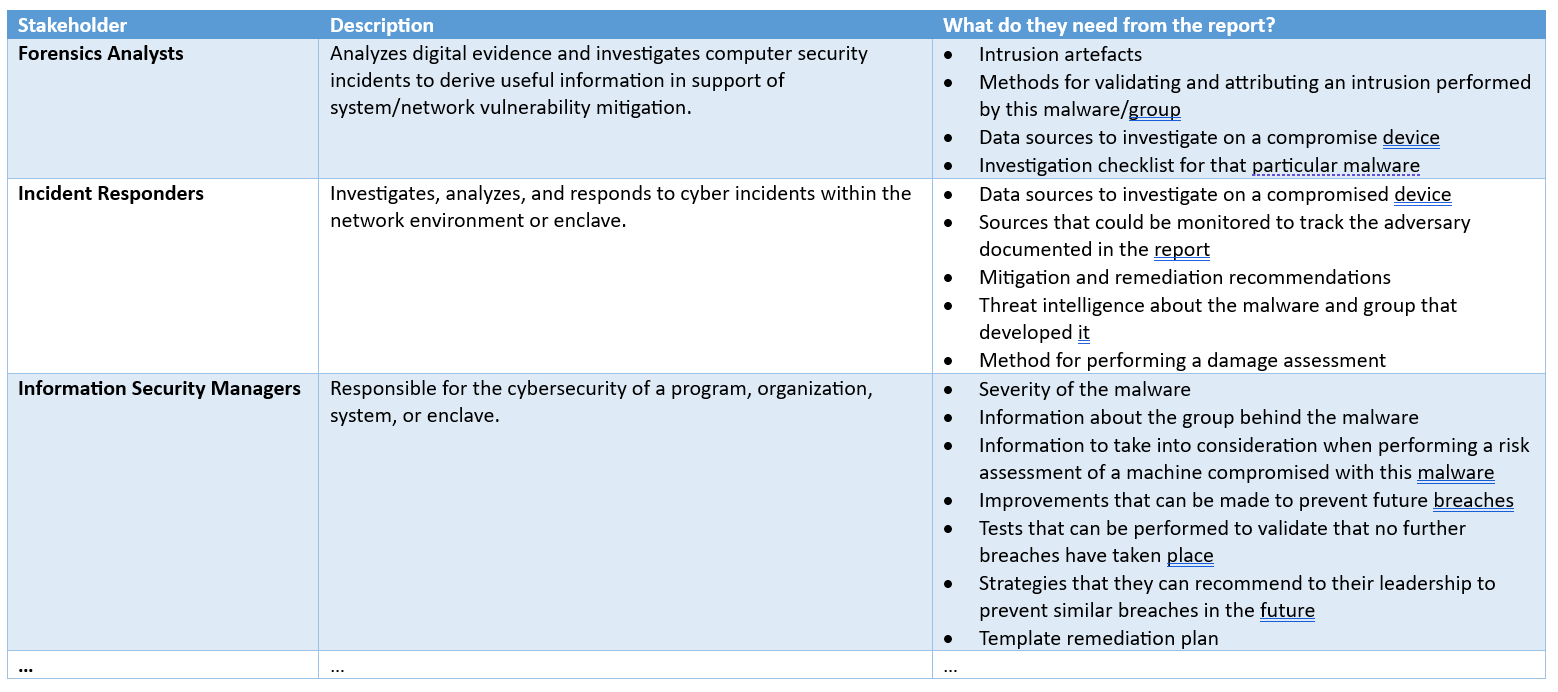
Refer to the NIST NICE or DCWF framework, which enumerates numerous cyber work roles and the responsibilities associated with each job, if you’re unsure about what each stakeholder requires.
Create a stakeholder checklist#
Having identified all stakeholders along with their respective needs and wants, the ensuing task is to construct a comprehensive checklist. This checklist will serve as an essential tool to ensure your report encompasses all necessary elements, addressing each stakeholder’s concerns effectively.
Individual Stakeholder Analysis: Begin by methodically reviewing each stakeholder. Examine their unique perspectives, requirements, and the potential impact the report will have on them. This detailed analysis will aid in understanding the varied expectations and information needs of each stakeholder group.
Categorization and Prioritization: Group and categorize the key components that are crucial for inclusion in your report. Sort these elements based on their relevance and significance to the different stakeholders. Prioritizing these components will facilitate a structured approach in addressing the most critical aspects of the report first.
Comprehensive Checklist Creation: With the prioritized elements in hand, construct a detailed checklist. This checklist should be designed as a verification tool to ensure that no critical component is overlooked. It should include specific items tailored to the interests of each stakeholder group, thereby guaranteeing a report that is thorough, relevant, and inclusive of all necessary perspectives.
Step 2 - Starbursting#
Starbursting is a powerful brainstorming technique used to generate questions about a particular subject. In the context of creating a cybersecurity report, it can be an invaluable tool for ensuring thorough analysis and comprehensive coverage. Here’s how to effectively use Starbursting to frame questions for your report:
Understanding Starbursting#
Starbursting involves visualizing a star with the central idea or topic in the middle and questions branching out like rays. Each ray represents a different question or line of inquiry about the central topic. This approach encourages in-depth exploration and uncovers various aspects of the subject that might otherwise be overlooked.
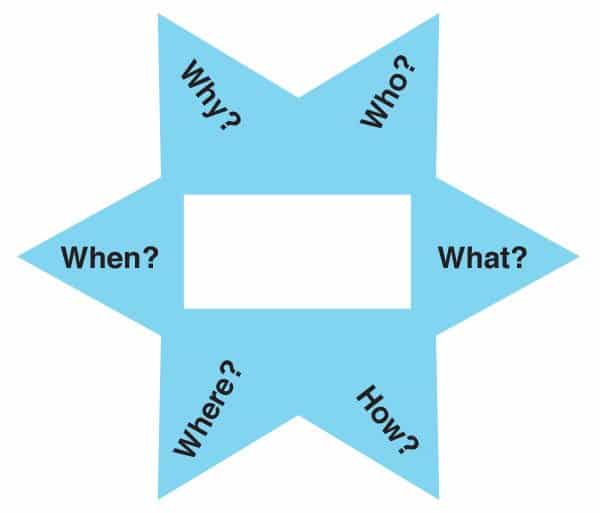
Steps for Implementing Starbursting:#
Identify the Central Topic: Place the main focus of your report at the center of the star. This could be a specific cybersecurity incident, a policy review, or a system assessment.
Generate Questions: Begin by framing questions around the five basic W’s: Who, What, When, Where, Why, and also How! For instance:
Who was impacted by the security breach?
What methods were used in the attack?
When was the vulnerability first detected?
Where are the gaps in our current security protocols?
Why did the incident occur, and what were the contributing factors?
How can we improve our defenses against similar threats?
Expand Beyond the Basics: After covering the fundamental W’s, delve deeper. Ask more specific questions that explore each aspect of the central topic. For instance, under “Who”, you might ask about the specific departments, external entities, or systems involved.
Organize and Prioritize Questions: Once a comprehensive set of questions is generated, organize them in a logical sequence. Prioritize the questions based on their relevance and importance to the objectives of your report.
Utilize Questions for Report Structure: Use these questions to structure your report. Each question can guide a section or part of your analysis, ensuring that your report is well-rounded and addresses all critical aspects of the topic.
Review and Refine: Finally, review the questions with stakeholders or team members. This can provide additional insights and ensure that the questions are aligned with the goals of the report.
By employing Starbursting, you can systematically dissect your cybersecurity topic, ensuring that your report is comprehensive, thoroughly addresses all pertinent questions, and meets the informational needs of your stakeholders. This technique not only aids in the initial stages of report planning but also enhances the overall quality and depth of your analysis.
Step 3 - Audience, Issue, Message, Storyline#
The AIMS model — Audience, Issue, Message, Storyline — is a framework that can guide the structure and content of your cybersecurity report to ensure it is impactful and understandable. Here’s how to use AIMS in greater detail:
Understanding Your Readers#
Conduct Audience Analysis: Gather intelligence on the demographics, knowledge level, interests, and needs of your report’s readers.
Define Objectives for Each Audience: Determine what each audience member needs to take away from the report.
Customize Communication Style: Adjust the technical language, data complexity, and report depth according to the audience’s expertise and relevance to their role.
Consider Audience Stakes: Tailor the report content to address the stakes involved for different audience segments, focusing on what matters most to them.
If you have done Stakeholder Analysis in Step 1, then the tasks in this section should already be done.
Articulating the Problem#
Present the Background: Provide context for the issue at hand by including relevant history.
Specify the Issue: Clearly define what the problem is, avoiding vague descriptions. Include how it was identified, its scope, and its impact.
Relevance to the Organization: Connect the issue to business outcomes or operational capabilities to underscore its importance.
Prioritize Issues: If there are multiple issues, prioritize them according to their impact on the organization.
Conveying Your Core Point#
Clarify Your Key Messages: Outline the key messages that address the issue. There should be a primary message and, if necessary, several supporting messages.
Ensure Consistency: Keep the key message consistent throughout the report to reinforce its importance.
Focus on Actionability: Craft messages that lead to clear conclusions or call to actions, guiding the reader on the next steps.
Be Solution-Oriented: Messages should provide or imply solutions or recommendations for the issue.
Structuring Your Narrative#
Develop a Logical Structure: Organize the content of your report in a logical sequence that builds your argument or story from the introduction to the conclusion.
Create a Strong Introduction: Set the stage with a compelling introduction that outlines the issue and why the report matters.
Provide Evidence and Analysis: Include data, analysis, and evidence that support your key message. Use visuals where appropriate to enhance understanding.
Construct a Persuasive Argument: Use the data and analysis to build a persuasive argument around your key message. End with Impact: Conclude with a summary of key points and clear recommendations that follow from your message.
Step 4 - Decomposition and Visualization#
When crafting a cybersecurity report, the incorporation of Structured Analytics Techniques (SATs) is essential to distill complex data and analytical processes into digestible formats that facilitate understanding. As you deconstruct your analysis and choose appropriate visual aids, consider the range of SATs at your disposal to clarify your findings and reasoning.
Chronologies and Timelines: Use these to establish the sequence of cybersecurity events or breach attempts. They are particularly useful for illustrating how an incident unfolded over time, helping the reader grasp the timeline of threat detection, response, and mitigation.
Sorting, Ranking, Scoring, and Prioritizing: These techniques allow you to categorize components by significance or urgency. For example, you might rank vulnerabilities detected in a system from highest to lowest risk, helping prioritize remediation efforts.
Matrices: Apply matrices to cross-reference and compare data sets, such as matching types of cybersecurity incidents against the affected assets or departments. This can uncover patterns or correlations that may not be immediately evident from text alone.
Mind Maps: Mind maps can be used to diagrammatically represent the relationships between various elements of a cybersecurity ecosystem or incident, making it easier to understand how different aspects of the system interconnect and influence each other.
Workflow Diagrams: These diagrams are critical for visualizing the flow of information or decision-making processes within cybersecurity operations. They can reveal the intricacies of data movement and the points where security measures are applied.
Process Maps: Process mapping is invaluable for dissecting and explaining the steps involved in cybersecurity protocols or incident response. It lays out the entire process, allowing the reader to see the flow of actions and identify critical stages.
Gantt Charts: Gantt charts are essential for depicting the schedule of project implementations or the timeline for addressing cybersecurity issues. They provide a visual timeline that pairs tasks with their projected or actual durations.
Incorporating SATs into Your Report#
Match SATs to Analysis: Choose SATs that best match the type of analysis you have conducted. For instance, use a matrix to depict a risk assessment, or a Gantt chart to outline a project timeline.
Reflect Your Analytical Journey: The selected SATs should reflect the analytical journey you undertook. If your analysis involved prioritizing issues, make sure this is reflected in your report through ranking or scoring visualizations.
Clarify the Data: Ensure each SAT clarifies the data it represents. A complex chart that requires extensive explanation may not be effective. Simplicity and clarity should be the goals.
Explain the Relevance: Accompany each SAT with a narrative that explains its relevance to the report. Why was this SAT chosen? What does it show? How does it relate to the conclusions or recommendations?
Integrate SATs Seamlessly: SATs should feel like a natural part of the report, not an afterthought. Integrate them into the flow of the narrative, ensuring they enhance rather than interrupt the story you’re telling.
By thoughtfully selecting and incorporating SATs into your cybersecurity report, you enable readers to trace your analytical steps and better understand the rationale behind your conclusions. Well-chosen SATs not only make the report more compelling but also bolster the credibility of your analysis by making it transparent and accessible.
Step 5 - Finalize the Table of Content#
Finalizing the Table of Contents (ToC) before diving into the actual writing of your cybersecurity report can be an invaluable strategy. It sets a clear framework and roadmap for your document, ensuring that all critical areas are covered systematically. Here’s how to approach this:
Establishing the Framework#
Outline Major Sections: Start by outlining the major sections of your report such as Executive Summary, Introduction, Analysis, Findings, Recommendations, and Conclusion. This will provide a backbone for your report.
Identify Key Topics: Under each major section, identify the key topics or subtopics you plan to cover. These will become your subheadings.
Ensure Comprehensive Coverage: Make sure your ToC covers all aspects of the cybersecurity topic you are addressing. This might include threat assessment, incident analysis, mitigation strategies, etc.
Structuring for Logical Flow#
Logical Sequence: Arrange your topics and subtopics in a logical order that will make sense to the reader. Typically, this will follow a chronological order or a problem-solution format.
Flexibility for Changes: Be open to rearranging sections as you delve deeper into the report writing. The initial ToC should serve as a guide, not a constraint.
Planning and Organization#
Detailed Subheadings: For complex sections, break them down into more detailed subheadings. This will help you organize your thoughts and ensure that each aspect of the topic is addressed.
Page Estimates: Assign tentative page numbers to each section and subheading. This will help in balancing the report and ensuring that adequate attention is given to each section.
Aligning ToC with Report Objectives#
Focus on Report Goals: Tailor the ToC to align with the primary objectives of your report. What do you want the reader to learn, understand, or decide after reading your report?
Feedback from Stakeholders: If possible, get feedback on the ToC from stakeholders or potential readers to ensure it meets their needs and expectations.
Using ToC as a Writing Guide#
Guiding Your Writing: Use the finalized ToC as a blueprint to guide your writing. It will help keep your report focused and organized.
Checking Completeness: As you write, use the ToC to check off sections you have completed. This can be satisfying and help maintain momentum.
Final Adjustments#
Be prepared to revise the ToC as your report takes shape. The process of writing can bring new insights that might require adjustments to the structure.
By finalizing the Table of Contents before starting to write, you lay a solid foundation for your cybersecurity report. It not only ensures a comprehensive and organized approach but also streamlines the writing process, helping you stay focused on the report’s objectives and scope.
Step 6 - Choice of Language and Sentence Structure#
In the composition of a cybersecurity report, the choice of language and sentence structure plays a pivotal role in ensuring clarity, readability, and effectiveness. Here’s how to approach this crucial aspect:
Clarity and Precision#
Use Clear and Precise Language: Opt for simple, direct language that conveys your message without ambiguity. Avoid jargon and technical terms unless your audience is familiar with them.
Define Technical Terms: When using industry-specific terms or acronyms, provide a definition upon first use. This practice is essential to keep your report accessible to all readers.
Objective and Unbiased#
Maintain Objectivity: Your report should be free from personal bias or preferences. Present facts and findings based on evidence, not opinions.
Neutral Tone: Keep a neutral and professional tone throughout the report, avoiding emotional or persuasive language where it is not appropriate.
Conciseness#
Be Concise: Aim for brevity in your sentences. Long, convoluted sentences can confuse readers and obscure your message.
Eliminate Redundancy: Avoid repeating the same information or using multiple words when one will do. This keeps the report focused and readable.
Strive for Clarity: Aim for clear, straightforward language that conveys your message effectively.
Sentence Structure#
Use Active Voice: Prefer the active voice over passive. Active voice makes your writing more direct and vigorous. For instance, say “The team resolved the issue” instead of “The issue was resolved by the team.”
Vary Sentence Length: Mix short and longer sentences to maintain the reader’s interest. However, be wary of overly complex or run-on sentences.
Tone and Formality#
Maintain a Professional Tone: Your report should reflect a formal and professional tone befitting a business or technical document.
Be Consistent in Tone: Ensure the tone remains consistent throughout the report. Sudden shifts in tone can distract or confuse the reader.
Accessibility#
Consider the Audience’s Background: Tailor the complexity of your language to the audience’s level of expertise. Technical details should be simplified for a general audience, while more technical readers might require in-depth analysis.
Use Analogies and Examples: When explaining complex cybersecurity concepts, analogies and real-world examples can be helpful in making the content more relatable and understandable.
Persuasiveness#
Where appropriate, use language that persuades the reader of your argument or recommendations. However, ensure that persuasion does not compromise objectivity or factual accuracy.
Audience-Centric#
Empathize with Your Audience: Understand the needs and knowledge levels of your audience. Tailor your report to be as effective as possible for them, whether they are technical experts or non-technical stakeholders.
Communicate, Don’t Confuse: Aim to inform and clarify, not to impress with complex jargon or technical prowess.
Review and Refinement#
Proofread for Language and Grammar: Carefully proofread your report to catch and correct grammatical errors, awkward phrasing, and typos.
Peer Review: If possible, have a colleague review your report for clarity and readability. Fresh eyes can often catch issues that you may have overlooked.
By thoughtfully considering your choice of language and sentence structure, you ensure that your cybersecurity report is not just informative but also clear, engaging, and accessible to your intended audience. Remember, the way information is presented can be just as important as the information itself.
Step 7 - Write the report#

Embarking on the writing journey of your cybersecurity report can be akin to setting off on a grand adventure in the digital realm. Picture yourself as a cyber-explorer, navigating through a landscape filled with intriguing data, mysterious code, and hidden cyber threats. Each word you write is a step on a path through this uncharted territory, each sentence a discovery, unraveling the complexities of cybersecurity. Your keyboard transforms into a trusty tool, helping you unearth secrets from realms of ones and zeros. As you weave together the technical details with narrative flair, your report becomes more than just a document — it’s a map for others to follow, a guide through the intricate and fascinating world of cybersecurity. With every paragraph, you’re not just informing your readers; you’re taking them on a thrilling expedition through the digital wilderness, filled with insights, revelations, and a dash of your unique style. So, fasten your seatbelt, ready your wits, and let the writing escapade begin!
TL;DR#
Before you write#
What is the primary objective of my report?
Which key topics and points are essential to include?
Who is my intended audience, and what are their informational needs?
How can I best organize and present the information to meet these needs?
To Do:
Compile a comprehensive list of key stakeholders involved or impacted by the report
For each listed stakeholder, develop a detailed inventory of their specific needs and expectations
Create an exhaustive checklist of elements required in the report to address and satisfy the identified needs and wants of all stakeholders
Generate a list of critical questions that the report must address, ensuring comprehensive coverage of the topic
Outline a list of necessary diagrams, images, tables, and figures that will effectively convey the report’s data and insights
Construct a preliminary Table of Contents that logically organizes the report’s content, facilitating ease of navigation and comprehension
Once your report is written#
Does my report exhibit a logical and clear structure?
Are all crucial topics adequately covered in the document?
Does the report provide all necessary information for the intended audience, supported by relevant evidence?
Have I identified and acknowledged any gaps in information?
Does the report culminate in a well-defined conclusion?
Is there any superfluous information that needs to be removed, or is there detailed content in the main text that would be more appropriate in an annex?
Is the document’s layout clear, and does it adhere to prescribed style guidelines?
Has the report undergone thorough proofreading for accuracy and clarity?
Complete Summary#
Craft cybersecurity reports that effectively communicate vital information for decision-making and strategy development
Apply universally applicable foundational principles and guidelines, regardless of the report’s specific context
Conduct thorough research on various cybersecurity report examples from reputable sources online.
Analyze and incorporate the most effective strategies, structures, and content styles from these examples.
Prioritize understanding and managing stakeholder needs and expectations
Analyze each stakeholder’s interests and concerns in relation to the report
Analyze individual stakeholders methodically for unique insights
Create a comprehensive checklist to address each stakeholder’s concerns effectively
Tailor reports to address the specific needs of varied stakeholders
Communicate necessary information effectively to both technical and non-technical stakeholders
Ensure that stakeholders can derive value from the report
Foster stakeholder engagement and action through the report
Enhance report relevance by understanding stakeholder perspectives
Balance technical detail with accessibility in reports
Inform report content and structure based on stakeholder analysis
Construct a detailed checklist with prioritized report components
Prioritize report elements based on their relevance
Enhance report relevance by understanding different perspectives
Communicate with diagrams, tables and charts:
Chronologies and Timelines
Sorting, Ranking, Scoring, and Prioritizing
Matrices
Mind Maps
Workflow Diagrams
Process Maps
Gantt Charts
Use this tone of language:
Concise
Factual
Clear
Substantiated
Unbiased
Professional
Proof read for errors
Only use jargon in technical sections of the report
