Enumerating Active Directory with Powerview
Contents
Enumerating Active Directory with Powerview#
In this blog post, we’ll introduce you to PowerView: a tool for active directory enumeration. We’ll cover windows Net command utilities
and, how PowerView can help you enumerate Active Directory objects. By the end of this post, you should have a good understanding of what PowerView is and how it can be used to enumerate Active Directory objects.
Windows Net Command utilities#
First, let’s remember some examples of helpful commands:
net view /domain: This command displays a list of all hosts in the specified domain.net user /domain: Displays a list of users.net accounts /domain: Displays the password policy.net group /domain: Displays a list of domain groups.net group "Domain Admins" /domain: Lists people in the group.net share: Displays the current number of SMB units.net session: This is used to examine SMB sessions.
Because net commands are incorporated into every Windows machine, understanding how to utilize them may be a valuable tool for testing Windows devices.
Querying Active Directory groups using PowerView#
PowerView is an extremely useful PowerShell tool for obtaining precise information on an organization’s Active Directory domain and forest.
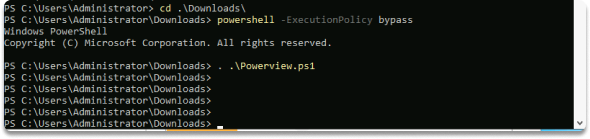
To utilize PowerView on our local machine, we first move the directory to where the PowerView module is located and disable PowerShell Execution Policy. The third command is then used to allow the use of PowerView with Powershell.
cd Downloads
powershell -ExecutionPolicy bypass
. .\PowerView.ps1
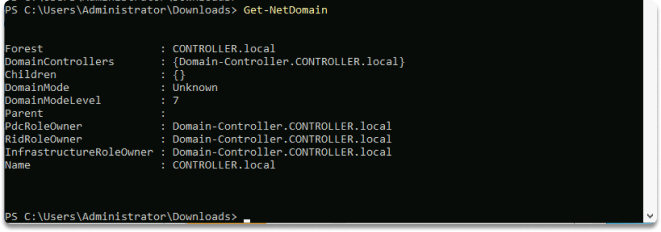
To retrieve information about your current domain run this command:
Get-NetDomain
In the following image, we get the forest and domain controller hostname.
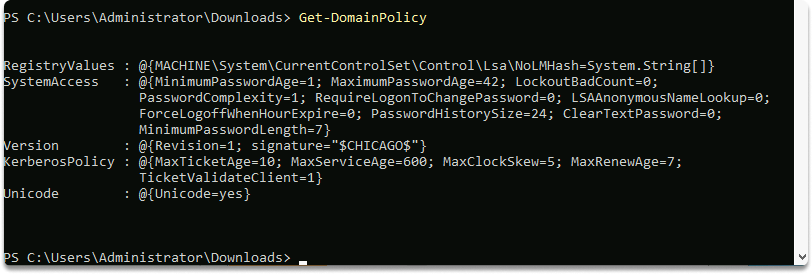
We can also get the list of the domain policies of the defined domain with this command:
Get-DomainPolicy
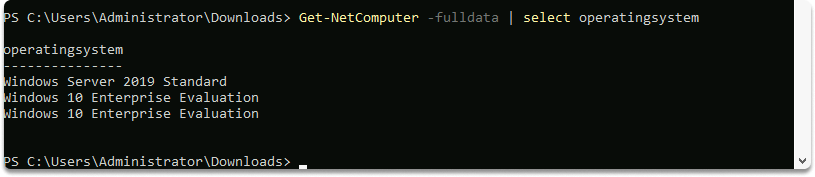
This command shows all operating systems on the domain.
Get-NetComputer -fulldata | select operatingsystem
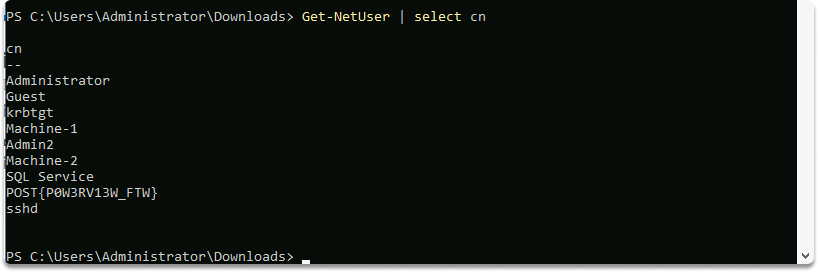
We can get a list of all users on the domain with this command:
Get-NetUser | select cn
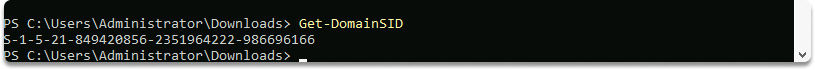
To retrieve the Security Identifier (SID) of the current domain, use the following command:
Get-DomainSID
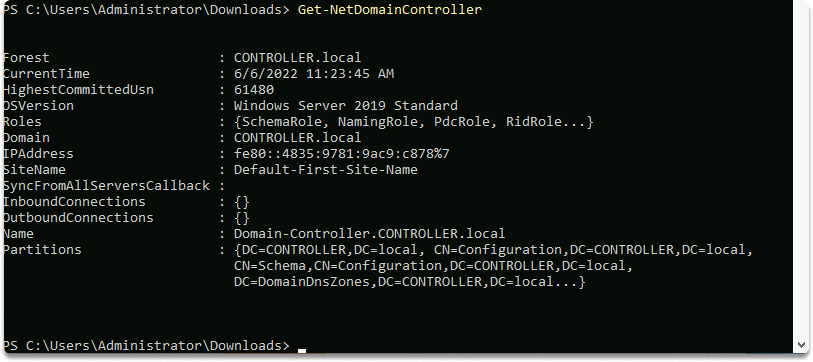
To easily retrieve the identity of the domain controller on the current domain, use the following command: Get-NetDomainController.
As shown in the following snippet, we got specific details about the domain controller such as its operating system, hostname, and IP addresses.
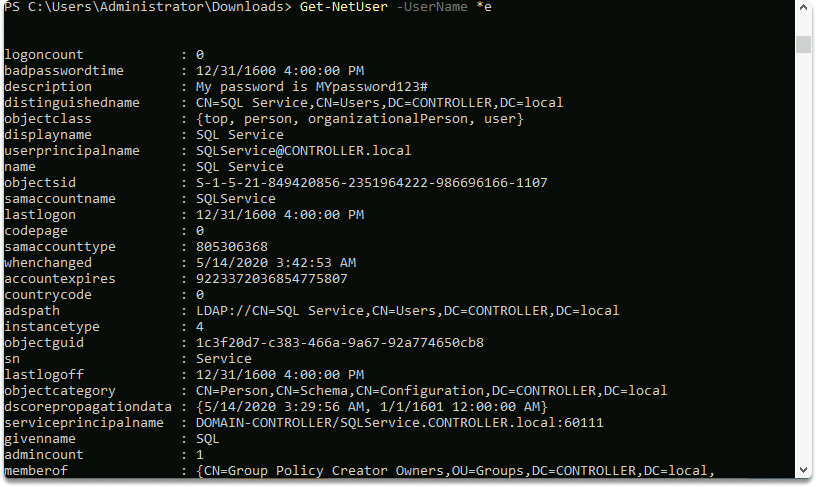
To get a list of all the users on the current domain, use the following command: Get-NetUser
As shown in the following screenshot, we listed all user names which has a lowercase e in their username.
To list all domain computer accounts on the current domain, use the following command: Get-NetComputer
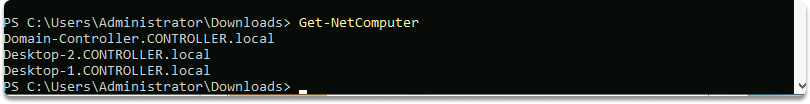
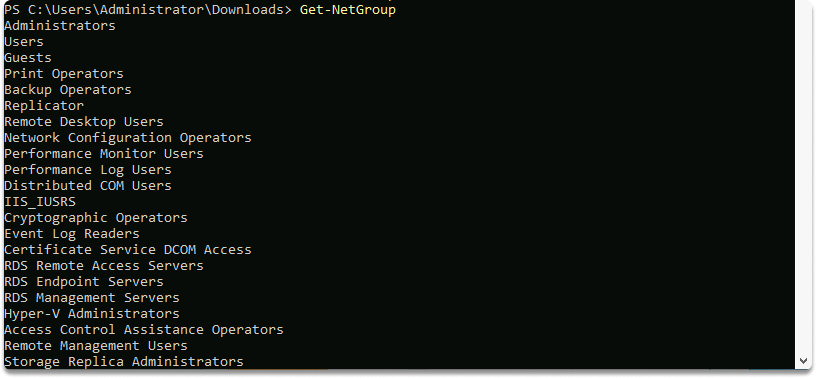
To list all the groups within the current domain, use the following command: Get-NetGroup.
As shown in the following screenshot, all the groups, and their details were retrieved:
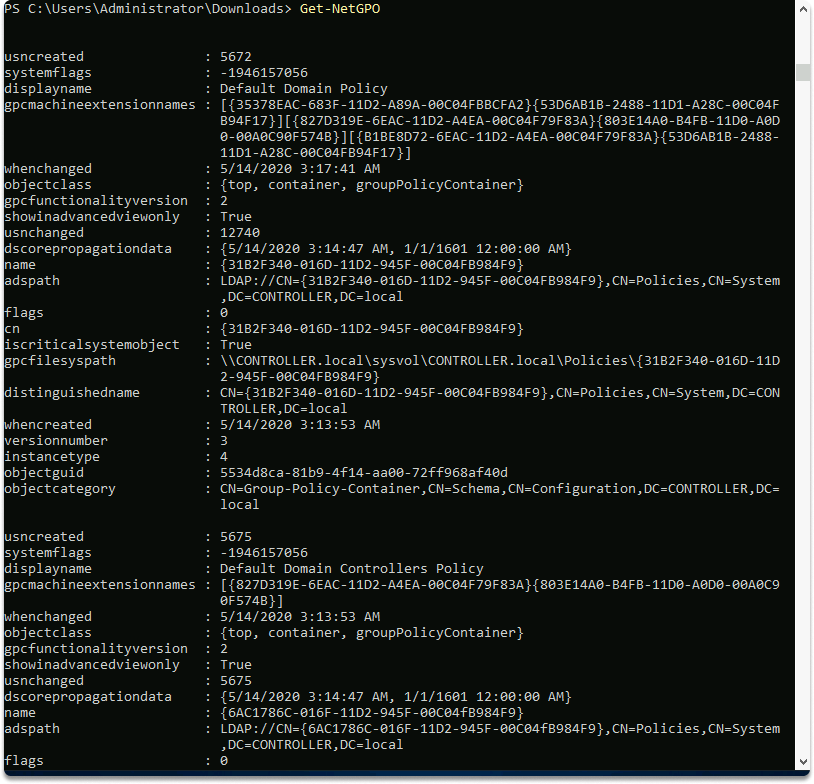
To get a list of all the GPOs from the current domain, use the following command: Get-NetGPO
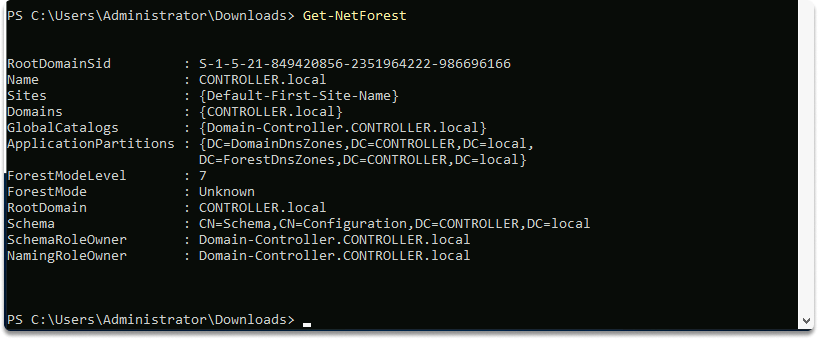
To get specific details about the current forest, use the following command: Get-NetForest. As shown in the following screenshot, we got information about the forest :
See also
Looking to expand your knowledge of penetration testing? Check out our online course, MPT - Certified Penetration Tester
