Enumerating SMTP with Metasploit
Contents
Enumerating SMTP with Metasploit#
SMTP, or Simple Mail Transfer Protocol, is a protocol used for sending and receiving email. It’s a key part of how email works, and it’s what allows you to send and receive messages from your email account. Metasploit is a powerful tool for exploit development and testing. It includes a wide range of features, including a comprehensive database of exploits and payloads, as well as a robust framework for developing and testing exploits. In this blog post, we’ll take a look at how Metasploit can be used to gather information about a target system via SMTP.
What is The Simple Mail Transfer Protocol (SMTP)#
The Simple Mail Transfer Protocol is the protocol used to send email which uses TCP port 25 in default. SMTP, like FTP, is a relatively ancient technology with little security in design. For that reason, SMTP has been targeted for years, and most organisations that host SMTP servers have learnt how to protect these servers against exploitation.
Taking advantage of SMTP vulnerabilities#
The most helpful SMTP attacks for a pentester are often coupled with a single susceptible SMTP server version.
Mail servers that are poorly configured or susceptible may frequently give an initial ingress point into a network, but before we begin an attack, we want to fingerprint the server to ensure that our pinpointing is as exact as possible.
To do this, we will employ MetaSploit’s “smtp version” module. Metasploit contains an SMTP enumeration utility in its list of auxiliary scanners. We will utilize auxiliary/scanner/smtp/smtp_enum.
It checks a range of IP addresses and evaluate the version of any mail servers it discovers. This list also contains a module named “smtp enum” as we see in the provided path. To use the module, you just need to provide it with an address or range of addresses to scan and a wordlist including names to list.
Let’s do a quick activity.
Quick hands-on excercise: Enumerate a vulnerable SMTP server#
Time estimated: 5 minutes
In this excercise, first we are going to discover if SMTP is running on a standard port on the target IP with this nmap. This command will produce the scan result with increased verbosity.
nmap -A -p- 10.10.3.242 -vv
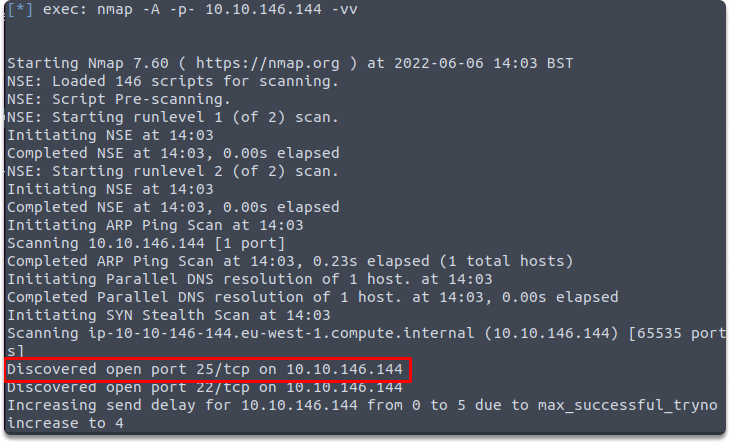
This image shows that SMTP is open in the target machine and running on a standard port which is 25.
After discovering what port we should be targeting, we can run Metasploit with this command: msfconsole
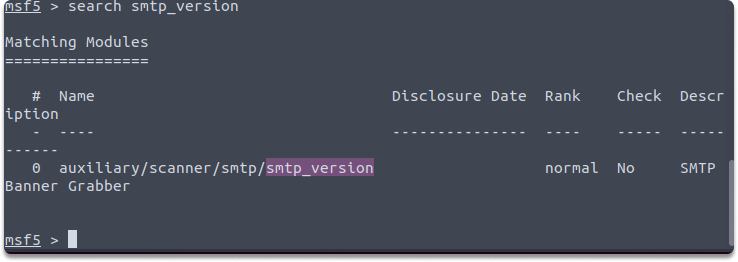
As a next step, running search smtp_version command gives us the module names and descriptions in Metasploit terminal.
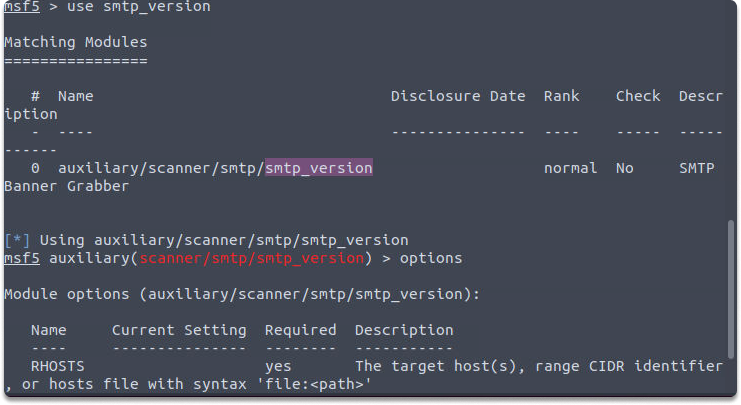
We can list the options of the current module by with interacting this command: use smtp_version and then typing options
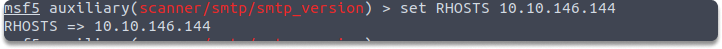
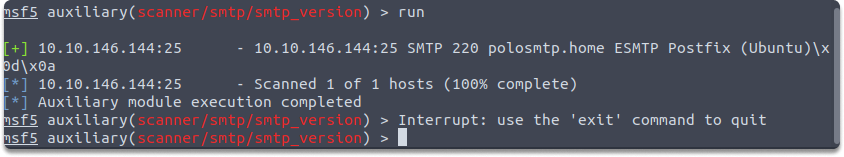
We can also set a value for our target machine: set RHOSTS 10.10.146.144 and then run this command: run
Successful output will also show the system mail name and what Mail Transfer Agent (MTA) is running.
See also
Looking to expand your knowledge of penetration testing? Check out our online course, MPT - Certified Penetration Tester
