Pass the Hash
Contents
Pass the Hash#
Pass the Hash (PtH) attack is a type of cyber-attack where an attacker steals the hashed password of a user from a compromised system and then uses that hashed password to authenticate as the user on another system without knowing the actual plaintext password. This attack takes advantage of the weakness of using hash values of passwords instead of the passwords themselves for authentication.
Here’s how Pass the Hash attack works:
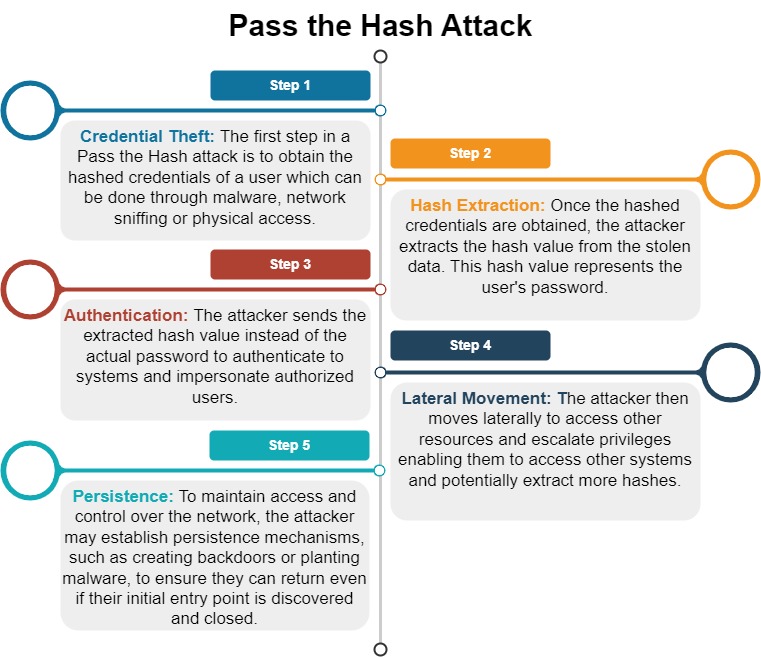
1. Password Hash Retrieval: The attacker gains access to a compromised system where the passwords are stored as hashes. These hashes can be obtained from local files or databases where user credentials are stored.
2. Hash Credential Theft: The attacker extracts the hashed password of a specific user from the compromised system.
3. Hash Authentication: Instead of trying to crack the hashed password to obtain the actual plaintext password, the attacker uses the stolen hash directly to authenticate on another system. Many systems use a form of Single Sign-On (SSO) where the same user credentials are used to access multiple systems. So, if the user’s credentials are valid on one system, they are also valid on other systems.
4. Elevation of Privileges: Once authenticated, the attacker can potentially escalate privileges and access sensitive information or perform unauthorized actions on the target system.
Examples of Pass the Hash Attack#
An attacker gains access to a Windows system and extracts the hashed password from the Windows Security Account Manager (SAM) or Active Directory (NTDS.dit) database. They use tools like Mimikatz to pass the hashed credentials and authenticate on another system within the same domain.
In a corporate network, an attacker gains access to a server where Linux user hashes are stored in the /etc/shadow file. They extract the hashed password and use it to authenticate as the same user on other Linux systems within the organization.
Countermeasures against Pass the Hash Attacks:#
1. Implement Multi-Factor Authentication (MFA): By using MFA, even if an attacker obtains the hashed password, they will still need an additional authentication factor (like a one-time password) to access the system, making it more difficult for them to succeed.
2. Limit Privileges: Follow the principle of least privilege and ensure that users have only the necessary access required to perform their tasks. This minimizes the potential damage an attacker can do if they gain access using Pass the Hash.
3. Store Passwords Securely: Use strong encryption and hashing techniques to protect password hashes stored in databases. Salting the passwords before hashing can also add an extra layer of security.
4. Regular Security Audits: Perform regular security audits to detect suspicious activity and unauthorized access attempts. Monitor logs for any signs of Pass the Hash attacks.
5. Patch and Update: Keep systems and applications up to date with the latest security patches to reduce the risk of initial compromise.
6. Detect and Block Pass the Hash Tools: Employ Intrusion Detection and Prevention Systems (IDPS) that can identify and block tools commonly used in Pass the Hash attacks, such as Mimikatz.
Final words#
By implementing these countermeasures, organizations can significantly reduce the risk of Pass the Hash attacks and enhance the overall security posture of their systems.
