Collision and Birthday Attack
Contents
Collision and Birthday Attack#
In the realm of cryptography and information security, collision and birthday attacks are two concepts of paramount importance. These attacks exploit the mathematical properties of hash functions, which are fundamental building blocks of modern cryptographic systems. This article delves into the intricacies of collision and birthday attacks, exploring their definitions, mechanisms, potential consequences, and mitigation strategies.
Hash Functions#
Before delving into collision and birthday attacks, it’s essential to understand the role of hash functions in cryptography. A hash function is a mathematical algorithm that takes an input (or ‘message’) and produces a fixed-size string of characters, which is typically a hexadecimal number. Hash functions are extensively used in various cryptographic applications, including digital signatures, password storage, message integrity verification, and more.
The primary characteristics of a hash function are as follows:
Deterministic: For the same input, a hash function will always produce the same output.
Fast Computation: Hash functions are designed to be computationally efficient, allowing for quick processing of data.
Pre-image Resistance: Given a hash value, it should be computationally infeasible to find the original input.
Collision Resistance: It should be difficult to find two different inputs that produce the same hash value.
Collision Attack#
A collision attack is a cryptographic attack that aims to find two distinct inputs that hash to the same output. In other words, the attacker seeks to identify two different messages that produce identical hash values when processed by the same hash function.
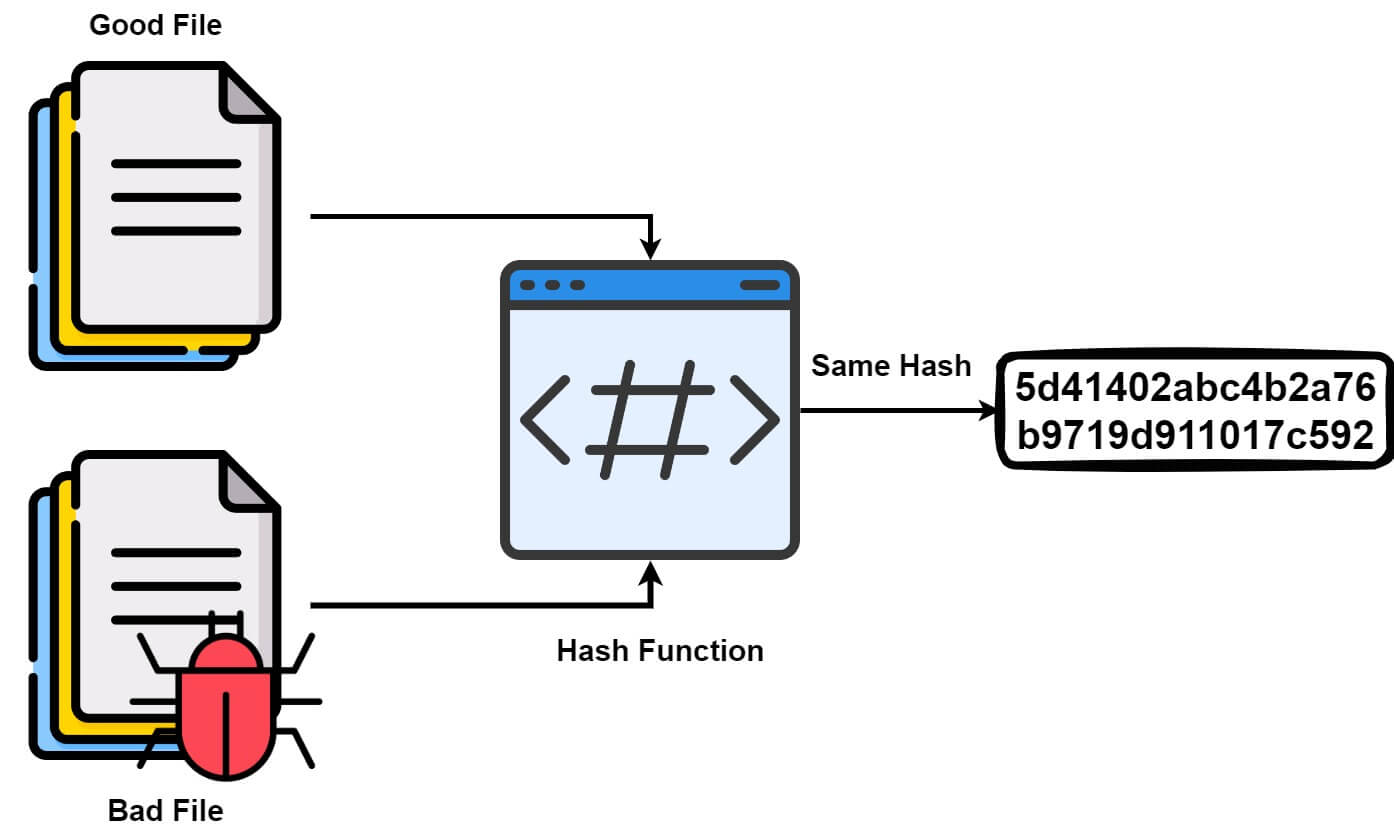
Mechanism#
In a collision attack, the attacker generates a large number of different inputs, computes their hash values using the targeted hash function, and stores these pairs of inputs and hash values. The attacker is essentially looking for a collision, which occurs when two distinct inputs produce the same hash value.
The mathematical underpinnings of a collision attack exploit the pigeonhole principle, which states that if you have more pigeons than pigeonholes, at least one pigeonhole must contain more than one pigeon. Similarly, in the context of hash functions, as the number of possible inputs is much larger than the number of possible hash outputs, collisions are inevitable due to the finite nature of the hash value space.
Consequences#
Collision attacks have severe implications for various cryptographic applications. For instance, consider digital signatures. If an attacker can find two different messages that produce the same hash value, they could potentially substitute one message for the other without altering the hash value, thus compromising the authenticity and integrity of the digital signature.
Example#
One prominent example of a collision attack is the MD5 (Message Digest Algorithm 5) hash function. In 2004, researchers successfully generated two distinct inputs that produced the same MD5 hash value. This discovery highlighted the vulnerability of MD5 and led to its depreciation in many security-critical applications.
Birthday Attack#
The birthday attack, also known as the birthday paradox, is a counterintuitive phenomenon that emerges from the mathematics of probability. It pertains to the likelihood of finding two inputs that yield the same hash value, even though the attacker is not explicitly seeking a collision.
Mechanism#
The name “birthday attack” is derived from the classic birthday problem in probability theory. The birthday problem poses the question: How many people are needed in a room for there to be a 50% chance that two of them share the same birthday? Surprisingly, the answer is only 23 people, which is lower than most people’s intuitive expectations.
In the context of hash functions, the birthday attack leverages the same principle. As the number of possible hash outputs is fixed, the probability of finding two different inputs that hash to the same value increases as more inputs are processed. This phenomenon arises due to the mathematics of combinatorics and the relatively small size of hash values compared to the potential number of inputs.
Consequences#
The birthday attack has significant implications for hash functions’ security. While it might seem that finding two different inputs with the same hash value is rare, the birthday paradox demonstrates that the probability of such an occurrence is higher than one might expect. This vulnerability can be exploited by attackers to degrade the security of hash-based applications.
Example#
Consider a cryptographic hash function with a 128-bit hash value. Intuitively, one might believe that finding two different inputs producing the same hash value would be exceedingly rare. However, using the principles of the birthday attack, the probability of a collision occurring in just 2^64 (approximately 18.4 quintillion) hash operations is already around 50%. This probability increases rapidly with more hash operations.
Mitigation Strategies#
To counteract collision and birthday attacks, cryptographic practitioners employ several mitigation strategies:
Use Strong Hash Functions: Select cryptographic hash functions that are designed to resist collision and birthday attacks. Algorithms like SHA-256 and SHA-3 are examples of widely used, strong hash functions that have undergone rigorous analysis.
Salting: In scenarios such as password storage, where hash functions are used, salting can thwart attacks. A unique random value (salt) is added to each input before hashing. This prevents attackers from using precomputed tables (rainbow tables) for quick hash value lookup.
Iterated Hashing: Applying a hash function multiple times (iterated hashing) can enhance security. However, the technique must be used with caution, as improper use might lead to performance and security trade-offs.
Keyed Hash Functions: HMAC (Hash-Based Message Authentication Code) is an example of a keyed hash function. It combines a secret key with the input data, making it significantly harder for attackers to find collisions.
Regular Algorithm Updates: Cryptographic algorithms, including hash functions, can become vulnerable over time due to advances in computing power and new attack techniques. Regularly updating to stronger algorithms is crucial to maintaining security.
Final Words#
Collision and birthday attacks underscore the importance of robust hash functions in modern cryptography. While the vulnerabilities they exploit arise from mathematical principles, the real-world implications are far-reaching. By understanding these attacks and implementing appropriate mitigation strategies, cryptographic professionals can better safeguard data integrity, digital signatures, and other security-critical applications. Staying informed about the latest advancements in hash function design and cryptographic techniques is essential for maintaining effective defenses against these types of attacks.
