Digital Signatures
Contents
Digital Signatures#
What is a Digital Signature?#
A digital signature is a cryptographic technique that enables the verification of the origin and integrity of a digital message, document, or data. It serves as a digital counterpart to a handwritten signature or a stamped seal in the physical world. The primary objectives of a digital signature are:
Authentication: Digital signatures verify the identity of the sender, ensuring that the message or document indeed originates from the claimed source.
Integrity: Digital signatures ensure that the content of the message or document has not been altered or tampered with during transmission.
Non-Repudiation: A sender cannot deny sending a digitally signed message, providing a means to hold parties accountable for their actions.
Digital signatures rely on asymmetric cryptography, also known as public-key cryptography. This involves two distinct keys: a private key and a public key. The private key is owned exclusively by the signer, while the public key is available to anyone who wishes to verify the signature.
How Does a Digital Signature Work?#
Digital signatures involve the use of public key cryptography. The sender uses their private key to sign the document, creating a unique digital signature. The recipient then uses the sender’s public key to verify the signature.
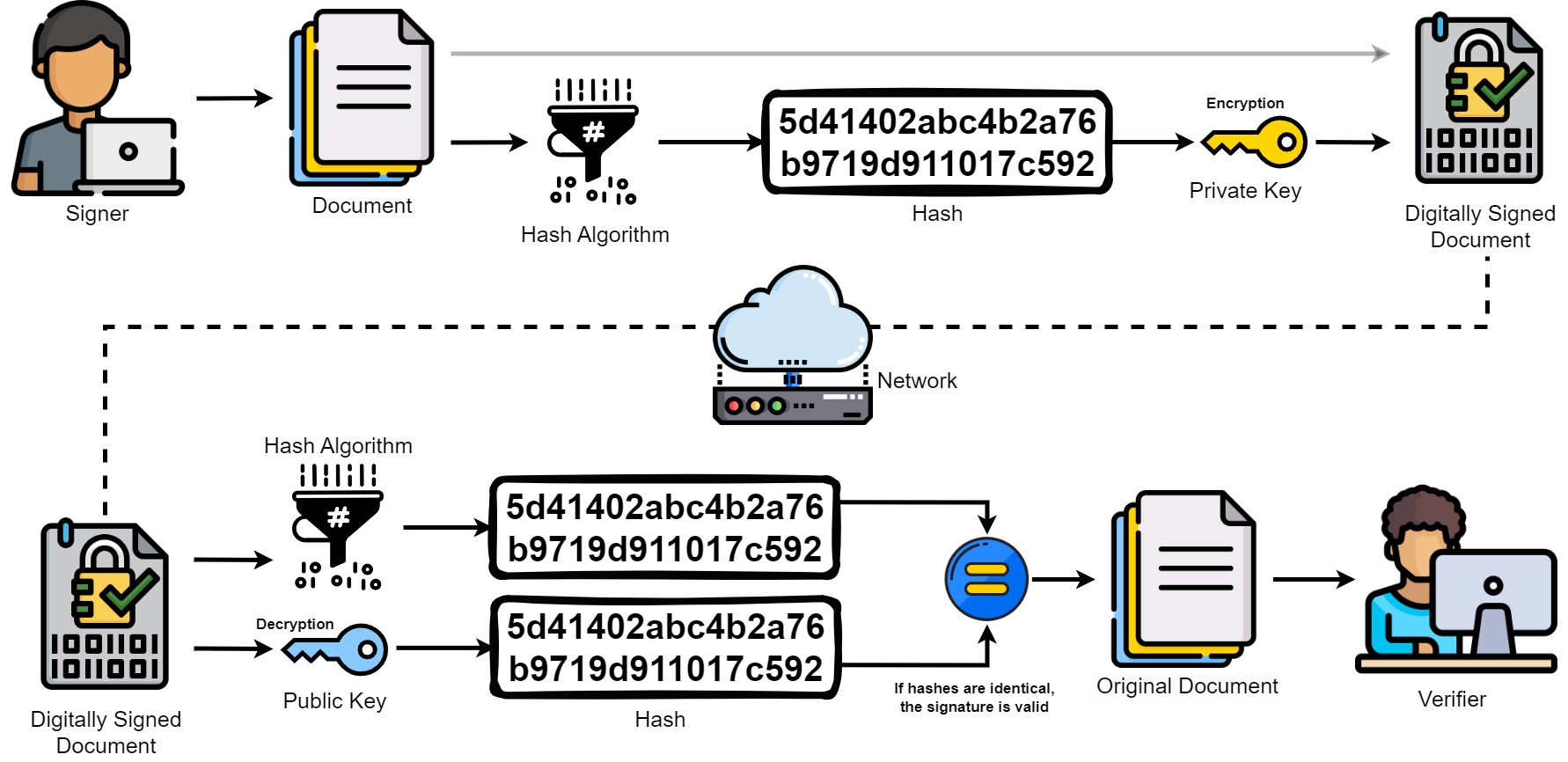
Creating a Digital Signature#
Generate Key Pair: The signer generates a cryptographic key pair consisting of a private key and a corresponding public key. The private key remains confidential and is known only to the signer, while the public key can be shared openly.
Hashing the Message: The message or document that needs to be digitally signed is processed through a hashing algorithm, which generates a unique fixed-length string of characters (hash value). This hash value represents the content of the message.
Signing the Hash: The signer uses their private key to encrypt the hash value of the message. This encrypted hash, known as the digital signature, is unique to both the message and the signer’s private key.
Attaching the Digital Signature: The digital signature is attached to the original message, creating a digitally signed document. This could involve appending the digital signature to the end of the document or embedding it within the document’s metadata.
Verifying a Digital Signature#
Extract Signature and Hash: The recipient of the digitally signed message extracts both the digital signature and the original hash value from the document.
Retrieve Public Key: The recipient obtains the public key of the signer from a trusted source or a digital certificate authority.
Decrypting the Signature: The recipient uses the signer’s public key to decrypt the digital signature. This produces a hash value that was originally encrypted with the private key.
Comparing Hashes: The recipient calculates a new hash value for the received message using the same hashing algorithm as the signer. They then compare this recalculated hash with the decrypted hash value obtained from the digital signature.
Validation: If the recalculated hash matches the decrypted hash, it indicates that the message has not been tampered with and the digital signature is valid. This means that the message was indeed sent by the claimed signer and has not been altered since it was signed.
Digital Certificates#
Digital signatures often rely on digital certificates issued by trusted Certificate Authorities (CAs). These certificates contain the sender’s public key and are used in the verification process.
Real-World Applications#
Digital signatures find application in various scenarios where ensuring the integrity and authenticity of digital data is crucial:
Email Communication: In email communication, digital signatures can be employed to verify the source of an email and detect any alterations made to its content during transit. This is particularly important in business communications and sensitive information exchanges.
Software Distribution: Digital signatures play a pivotal role in the distribution of software and updates. Software developers sign their code with a digital signature, allowing users to verify that the software has not been tampered with by malicious actors.
E-Commerce and Online Transactions: Digital signatures are used to authenticate electronic contracts, invoices, and financial transactions in the realm of e-commerce. They provide a layer of trust between parties engaging in online transactions.
Government and Legal Documents: Governments and legal institutions use digital signatures to authenticate and validate official documents, such as contracts, permits, and licenses. This accelerates administrative processes and reduces paperwork.
Ensuring the Security of Digital Signatures#
While digital signatures offer robust security, several vulnerabilities and challenges must be addressed to ensure their effectiveness:
Key Management: The security of digital signatures heavily relies on proper key management. If a private key is compromised, an attacker could impersonate the legitimate signer. Key storage, protection, and regular rotation are essential to mitigating this risk.
Algorithm Strength: The security of digital signatures is closely tied to the strength of the underlying cryptographic algorithms. As computing power evolves, older algorithms can become vulnerable to attacks. Regularly updating algorithms is necessary to stay ahead of potential threats.
Revocation and Expiry: In cases of key compromise or personnel changes, mechanisms for revoking or expiring digital signatures and keys are crucial. Failure to do so could lead to unauthorized use or forged signatures.
User Awareness: Users should be educated about the importance of digital signatures and how to recognize valid signatures. Without proper awareness, users might be susceptible to phishing attacks or accept forged signatures.
Final Words#
In the digital age, where information and data form the backbone of modern communication and transactions, the assurance of authenticity, integrity, and accountability is paramount. Digital signatures, based on the principles of cryptographic security, provide a robust mechanism to meet these requirements. From securing email communications to enabling safe software distribution and e-commerce, digital signatures have woven themselves into the fabric of our interconnected world.
As we navigate an ever-evolving threat landscape, the role of digital signatures in cybersecurity becomes even more critical. By understanding the technology, applications, and challenges associated with digital signatures, individuals, businesses, and governments can harness their power to establish trust and security in an increasingly digital and interconnected ecosystem.
