Replay Attacks
Contents
Replay Attacks#
In today’s interconnected digital world, where the majority of our transactions and interactions take place online, ensuring the security of data and sensitive information is of utmost importance. Cyber attackers continually devise new ways to exploit vulnerabilities in applications and systems. Among the various cybersecurity threats, one that has gained prominence is a replay attack. This article will discuss what replay attacks are, how they work, their potential consequences, and most importantly, how developers and businesses can defend against them.
What are Replay Attacks?#
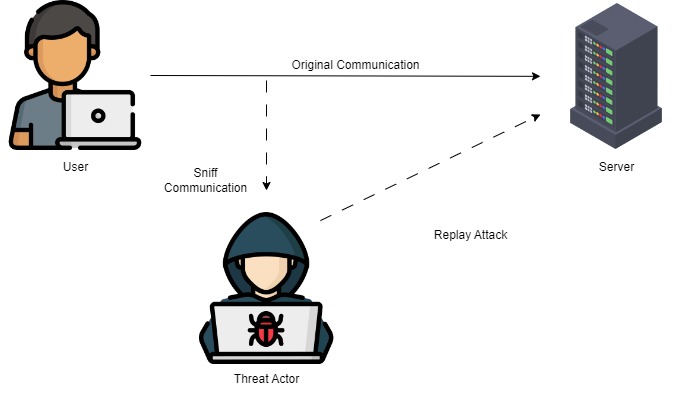
A replay attack is a form of cyber-attack in which an adversary intercepts and records a sequence of packets exchanged between a client and a server during a legitimate transaction. The attacker then replays these recorded packets at a later time to replicate the original transaction, tricking the system into accepting the repeated actions as valid.
The concept behind a replay attack is relatively simple: if an action or data transmission was valid before, it is likely to be considered valid again in the future, leading to unauthorized and potentially malicious outcomes. For instance, imagine a scenario where a user makes a secure online payment for a purchase. During the payment process, packets containing transaction details and authentication information are sent across the network. If an attacker intercepts these packets and replays them, the payment system may process the transaction again, resulting in the recipient receiving double the payment.
How Do Replay Attacks Work?#
Replay attacks exploit the inherent statelessness of many digital interactions. Stateless systems do not maintain information about previous events or sessions, making them susceptible to malicious exploitation. When an attacker captures packets during a legitimate transaction, they are essentially obtaining a snapshot of that particular event. By replaying this snapshot later, the attacker can recreate the entire transaction, as the system treats the repeated event as genuine.
Session Replay#
Session replay is the replication of a visitor’s experience on a website. Session replay, while conceptually similar to replay attacks, can have legitimate uses in specific scenarios. When a user connects to a web server, a session is formed. This session comprises various interactions between the client and the server. Session replay involves the re-creation of these interactions after they have occurred.
In some instances, session replay can be beneficial for analysis and debugging purposes. It provides valuable insights into the functioning of web-based client/server interactions, helping developers identify and fix issues in their applications. However, there are instances where session replay can pose a threat, particularly in transactional systems involving sensitive data. For instance, in a banking transaction, the ability to replay a session after the fact can lead to unauthorized access to user accounts or fraudulent activities. Therefore, for transactional systems, implementing replay prevention measures becomes crucial.
Session Replay Implementation and Drawbacks#
Most of the content and transactions in the digital system are stateless. Due to the statelessness, the system does not inherently possess information about the origin of requests or the destination of responses. To make replay work effectively, it is necessary to capture and store relevant data about interactions to enable later replay. Replay can be managed from either the client side (the user’s device) or the server side (the central server). Each approach has its advantages and disadvantages.
When managing replay on the server side, the system captures data based on the history of requests received. This approach is effective in recreating the interactions on the server but may not provide detailed information about client-only activities, such as mouse movements or user interface interactions specific to the user’s device.
On the other hand, when managing replay on the client side, tags are used to capture details of pages or interactions. This approach provides more comprehensive information about the client-side activities, including user interface details. However, it is important to note that any data originating from the client is vulnerable to manipulation, as it is under the control of the client and can be modified or obstructed before reaching the server.
Replay Attacks Mitigation Strategies#
Replay attacks can be effectively thwarted through a diverse array of defenses. It is crucial for developers to adhere to best practices, as inadequately implemented systems may lack the necessary replay protections, thereby allowing this attack vector to persist.
- Timestamps and Nonces: Utilizing timestamps and nonces (random numbers used only once) in packets can help verify the validity of requests. The system checks the timestamp to ensure that the request is current and not an old, replayed one.
- Sequence Numbers: Assigning a unique sequence number to each transaction helps the system detect and reject repeated or out-of-sequence requests.
- One-Time Tokens: Implementing one-time tokens in transactions ensures that each token is generated uniquely for a specific transaction and becomes invalid after use, preventing replay attacks.
- Session Tokens: Using session tokens to tie multiple requests together can help prevent replay attacks within a single session. These tokens are invalidated after the session ends, mitigating the risk of replays.
- Encryption and Digital Signatures: Encrypting sensitive data and using digital signatures can help ensure data integrity and authentication, making replay attacks much more difficult.
- Time Window Limits: Setting time window limits for requests prevents acceptance of outdated or delayed packets.
Conclusion#
Replay attacks pose a significant threat to the integrity and security of applications and systems, potentially leading to financial losses, unauthorized access, and data compromise. By incorporating preventive measures, application developers can fortify their systems against replay attacks. Alongside these technical measures, user awareness and education on secure practices can also contribute significantly to thwarting replay attacks and ensuring a safer digital environment.
