MCSI #015: Not receiving good feedback from your work? Here’s how to become exceptional
Contents
MCSI #015: Not receiving good feedback from your work? Here’s how to become exceptional#
In the field of cybersecurity, one of the major challenges faced by students and professionals alike is securing job opportunities and career advancement. Often, despite possessing the required qualifications, candidates are overlooked due to a perception of inadequate skills. While decision-makers may not directly express this, terms such as “not suited for the role” or “we found a person with additional competencies” often signal the underlying message of the candidate’s skills being below expected standards.
In this newsletter, we aim to address this issue and provide you with effective tactics and strategies to overcome this obstacle.
What does “industry standard work” mean?#
In the cybersecurity industry, there are certain expectations that are not always explicitly stated. For instance, if you are tasked with creating a script, it is assumed that you will produce professional documentation without being provided with a checklist of what that entails.
While this may seem unfair to some, it is a reality of the industry that professionals must navigate. Rather than dwelling on the perceived unfairness, we encourage you to accept this as a challenge and find ways to excel within this environment.
At MCSI, we offer numerous guidelines to assist students in learning how to produce work that meets industry expectations:
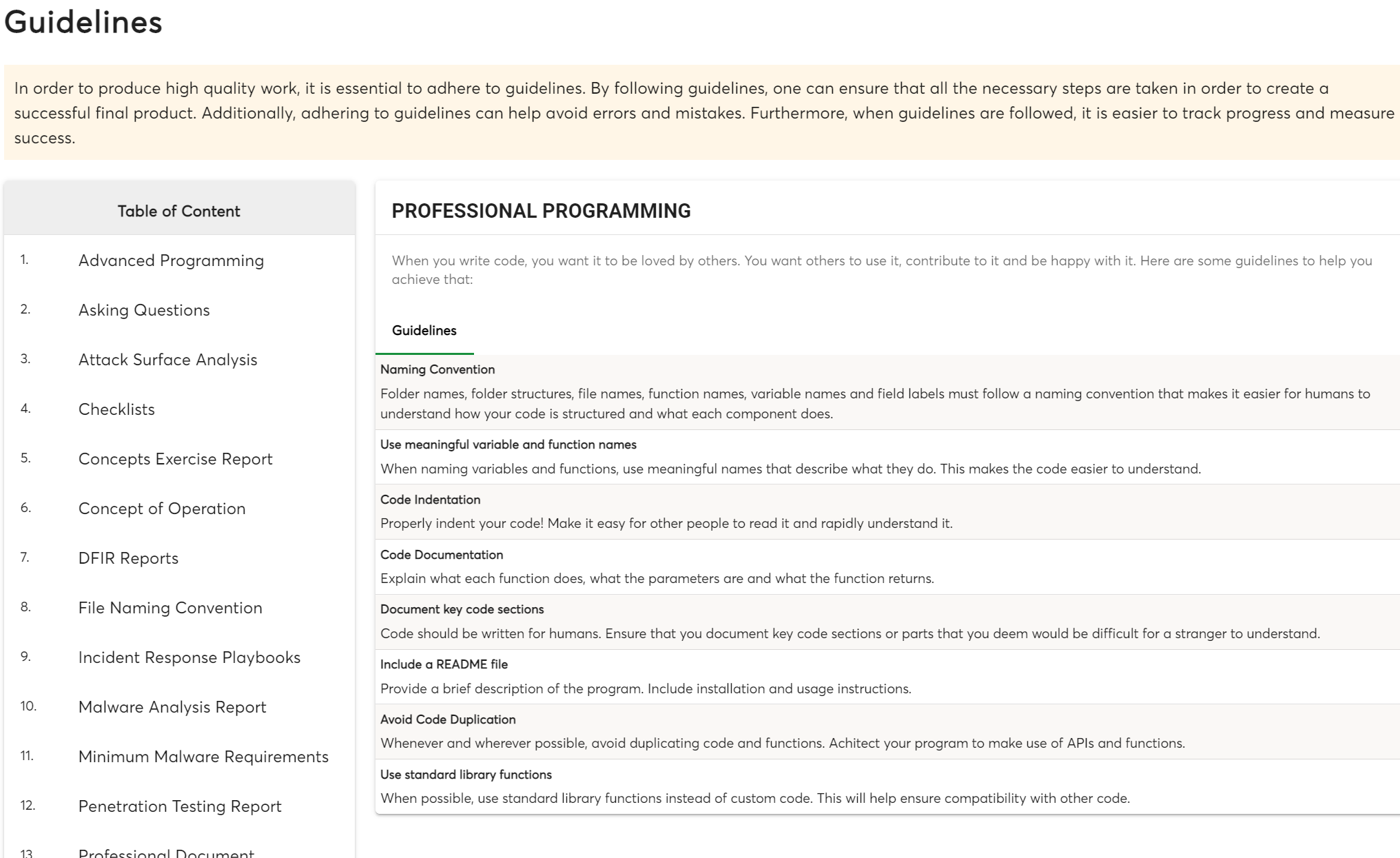
This is what sets us apart from other training providers who solely concentrate on whether or not students arrived at the right or wrong answer to an exercise. As we have emphasized, the quality of how the work is accomplished and the final product is just as important as discovering the “correct” answer.
How can I know what the industry expects of me?#
If you are new to the cybersecurity industry, it can be challenging to understand what is expected of you and how to produce work that meets industry standards. To address this, we recommend registering for the MCSI platform where you can solve simple exercises for free while meeting our guidelines and receiving feedback from instructors to ensure a minimum quality level for each submission.
Once you have a basic understanding of industry expectations, you can move on to a more advanced method. Let’s use an exercise on the platform to learn this method:
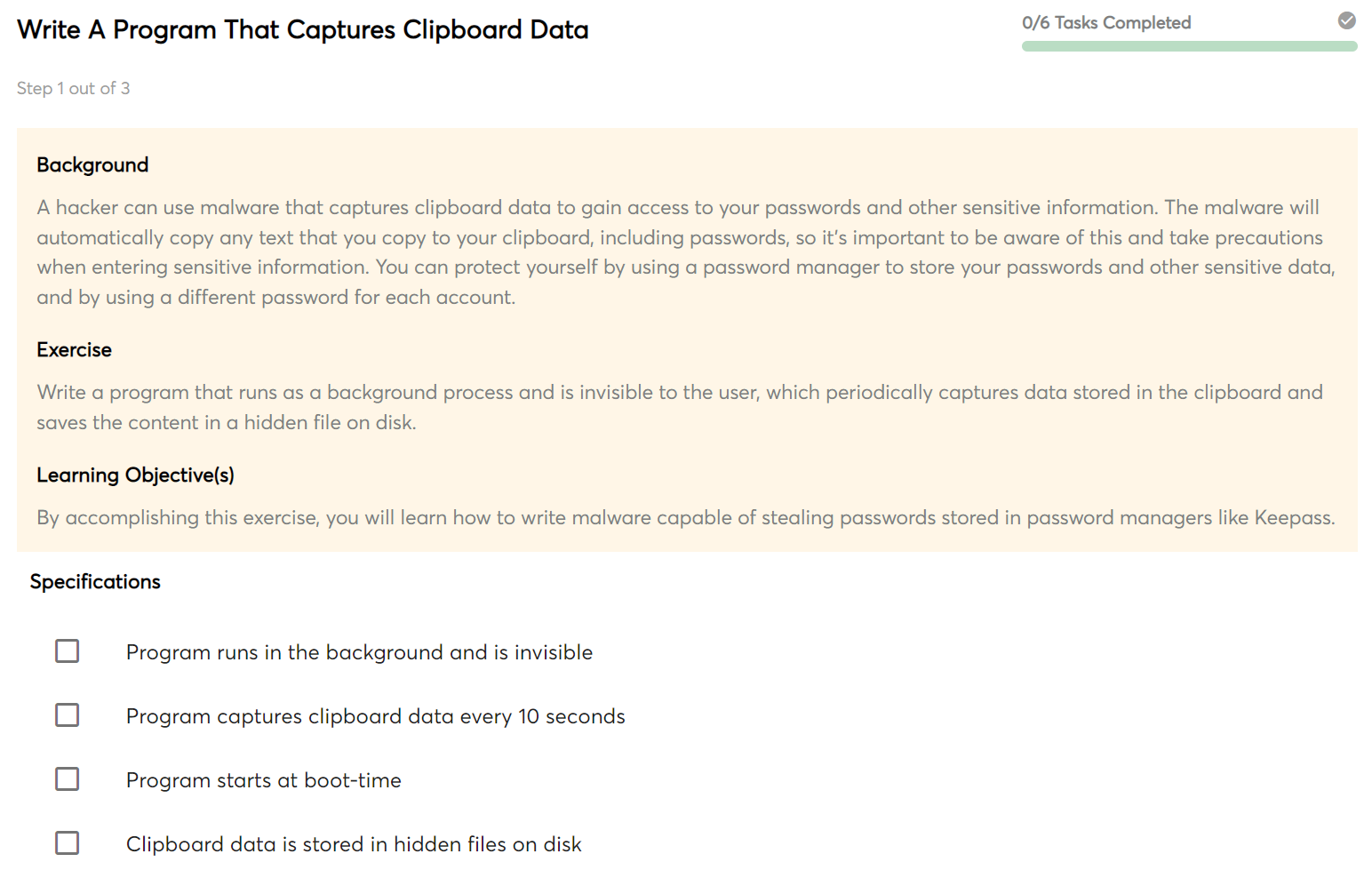
Consider this scenario
You are a member of a team responsible for conducting attack simulations to identify vulnerabilities in networks before malicious actors do. As a junior team member, your supervisor has requested that you develop a software program to steal passwords copied and pasted from note files or password managers. The supervisor has provided you with an email containing four specific requirements, as illustrated in the image above. Your task now is to develop this program and ensure that it adheres to industry standards.
This exercise presents a realistic scenario where your supervisor assigns a task with high expectations but without providing a detailed list of instructions. This approach allows you to showcase your problem-solving and critical thinking abilities, essential skills in the cybersecurity industry. As a professional, you are expected to be able to work independently, meet the desired outcomes, and produce high-quality work that aligns with industry standards.
Step 1 - Identify the stakeholders#
It is essential to begin any project by identifying all the stakeholders that may be affected by the work produced. For this exercise, the stakeholders are:
Your supervisor
Senior team members who will use the program
Future recruits who will learn how to use the program
The client who will have the program executed on their machines
This initial step should inspire ideas and prompt further considerations about the final product’s design. It is clear that coding a simple script will not be sufficient to produce a program that meets industry standards and exceeds expectations.
Step 2 - List the stakeholders’ needs and wants#
The second step in our process involves developing a comprehensive list of requirements that are tailored to each stakeholder. We accomplish this by setting aside a dedicated period of brainstorming, lasting anywhere from 30 minutes to an hour, during which we consider the specific needs and desires of each stakeholder. This approach allows us to produce a detailed and accurate list of requirements that is customized to the needs of each stakeholder.
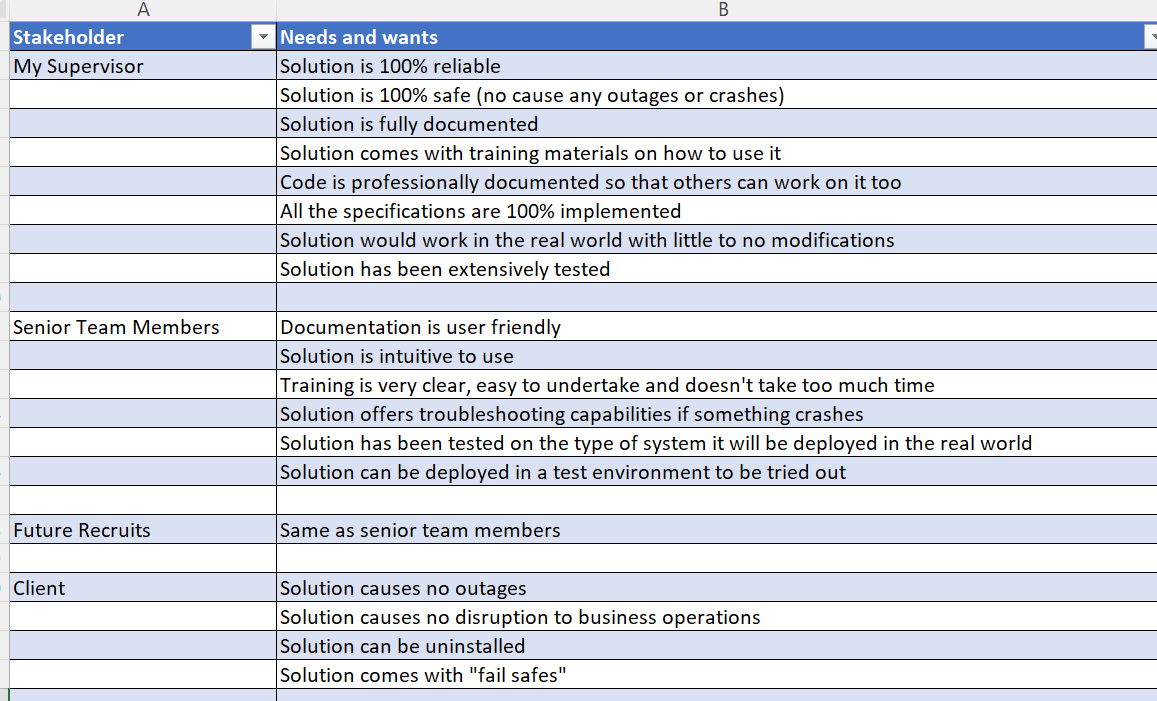
In real-world scenarios, the number of requirements developed can be extensive. However, in this newsletter, we thought it would be better to provide an easy-to-read and understandable image rather than overwhelming you with a complex list.
Step 3 - Imagine the ideal solution#
The final step involves translating the identified requirements into software specifications. Although the initial 4 specifications provided by your supervisor may seem limited, identifying stakeholders and their respective requirements has uncovered additional, “unspoken” requirements that need to be accounted for. To provide an ideal solution that meets industry standards, we would develop a comprehensive list of specifications.
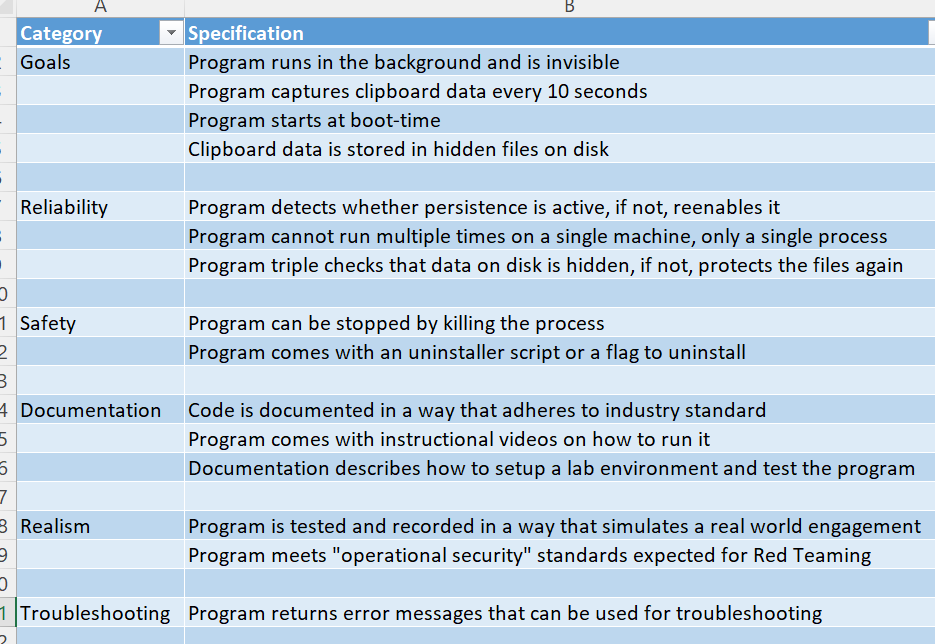
It’s impressive to see how much additional detail and consideration you have to put into your work by identifying the unspoken requirements and translating them into software specifications. This level of understanding and attention to detail is exactly what the industry expects from cybersecurity professionals!
How should I present the final product?#
On the MCSI platform, the final product typically takes the form of a video demonstrating the program’s functionality within a virtual machine. The most effective videos are those that showcase the program in action, as if it were being used in a real-world scenario, rather than simply highlighting each individual specification. As an excellent illustration, please take a moment to view the following example video created by Karun Thomas:
Karun’s submission to the MCSI platform showcases his dedication and attention to detail in developing a Red Team program that mirrors real-world scenarios. He went above and beyond by creating a dropper for his program that captures screenshots, in addition to well-documented code and a detailed video explanation. His efforts resulted in him being awarded the Gold Trophy, reserved for exceptional submissions that truly meet industry standards.
When you’re ready, this is how we can help you#
MCSI offers certifications that can teach you how to produce exceptional work in the field of cybersecurity. Our unique approach ensures that you are held accountable and systematically guided to meet industry standards. If you’re ready to start your journey towards becoming a skilled professional, visit our website to learn more about our certifications.