MCSI #017: Stakeholder Analysis - a powerful method to understand what people want and need
Contents
MCSI #017: Stakeholder Analysis - a powerful method to understand what people want and need#
Do you often feel overwhelmed by the complexities of managing cybersecurity projects? Are you juggling conflicting priorities, facing resistance from various parties, or struggling to secure buy-in from key stakeholders? You’re definitely not alone in these challenges.
In this newsletter, we’ll delve into Stakeholder Analysis, a valuable technique that can help you address and overcome these pain points. By effectively identifying and understanding the interests, expectations, and concerns of everyone involved, you’ll be able to build a more cohesive strategy that gains support from all corners of your organization. This approach not only streamlines your cybersecurity initiatives but also fosters a more collaborative and efficient work environment. Don’t let these hurdles hold you back – read on to discover how Stakeholder Analysis can be a game-changer in your cybersecurity endeavours.
What is Stakeholder Analysis and what will it help me with?#
Stakeholder Analysis is a systematic process of identifying and evaluating the needs, interests, and influence of key individuals or groups that have a stake in a project or decision. This process helps us better understand and address their concerns while shaping our cybersecurity strategies.
One of the key benefits of Stakeholder Analysis is achieving strategic alignment. By understanding the priorities and expectations of key stakeholders, we can ensure that our cybersecurity initiatives are in line with our organization’s goals. This leads to better decision-making and resource allocation, ultimately strengthening our security posture.
In addition, Stakeholder Analysis aids in effective communication. When we’re aware of each stakeholder’s priorities and concerns, we can tailor our messaging to resonate with them. This targeted approach not only fosters trust and understanding but also facilitates collaboration between different teams or departments working on cybersecurity projects.
Lastly, Stakeholder Analysis supports risk management. A comprehensive understanding of stakeholders allows us to anticipate potential challenges or objections, helping us address them proactively. This proactive approach can significantly reduce the likelihood of unforeseen issues, contributing to more robust and resilient cybersecurity strategies.
Who are the stakeholders?#
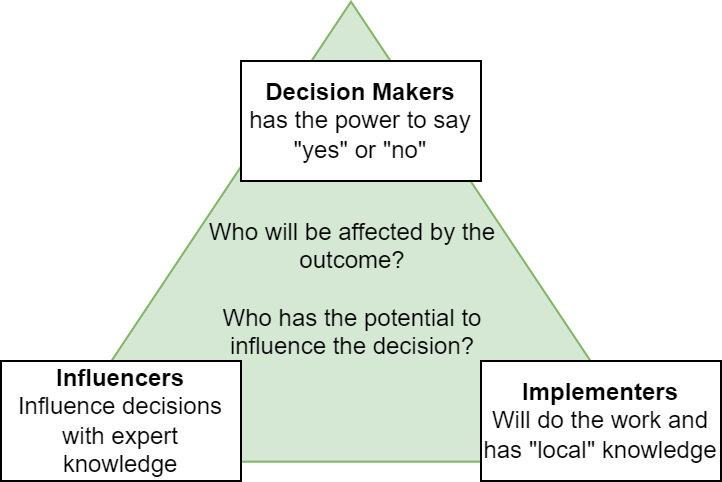
In our quest to understand Stakeholder Analysis better, it’s essential to identify who the stakeholders are in a cybersecurity context. One useful way to categorizes them into three main groups: Decision Makers, Influencers, and Implementers.
Decision Makers: These stakeholders are responsible for making the final decisions on cybersecurity initiatives, policies, and strategies. They may include top executives, such as the CEO, CIO, or CISO, as well as board members who have a direct impact on the direction of an organization’s cybersecurity program. Their primary role is to approve and support plans based on input from the other stakeholder groups.
Influencers: This group consists of individuals who can shape the decision-making process, even though they might not have the authority to make the final call. Influencers can be both internal and external to the organization. Internal influencers may include IT managers, cybersecurity team leads, or legal and compliance personnel, while external influencers might encompass industry experts, regulators, or even key customers. Their opinions, expertise, and guidance can significantly influence the decisions made by the Decision Makers.
Implementers: Implementers are responsible for putting cybersecurity plans and strategies into action. They play a crucial role in the day-to-day management and execution of cybersecurity initiatives. Implementers can include IT staff, cybersecurity professionals, system administrators, and even employees who follow security best practices in their daily tasks. Their hands-on experience and understanding of technical challenges can provide valuable insights to shape effective cybersecurity measures.
How do I perform Stakeholder Analysis and use the insights discovered?#
Moving on to the crucial part of Stakeholder Analysis, let’s explore how to perform it effectively. Here’s a step-by-step guide to conducting a thorough Stakeholders Analysis in the realm of cybersecurity:
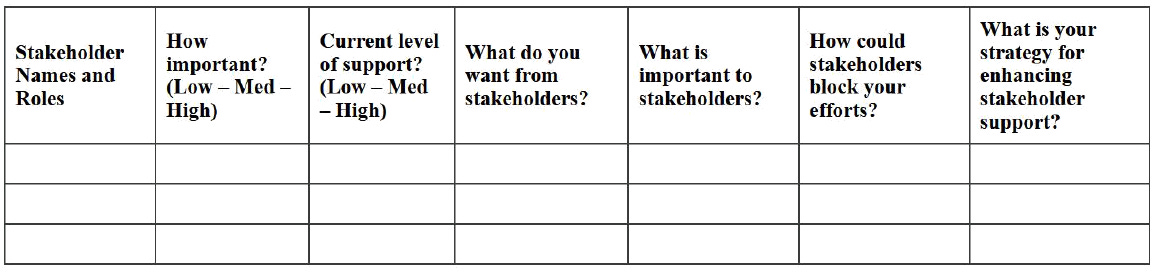
Identify your stakeholders: Begin by listing all the individuals, groups, or organizations who may be impacted by or have influence over your cybersecurity project. Remember to include both internal and external parties, such as employees, management, vendors, customers, and regulatory authorities.
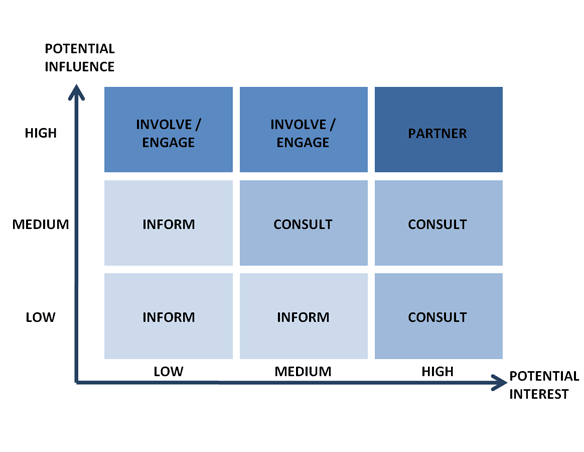
Prioritize stakeholders: Once you have your list of stakeholders, assess their level of interest and influence on the project. This will help you prioritize your efforts and allocate resources effectively. A simple way to do this is to create a stakeholder matrix, plotting each stakeholder based on their level of interest and influence.
Understand stakeholder needs and expectations: Gain insights into each stakeholder’s concerns, goals, and motivations. This will help you tailor your communication and engagement strategy to address their specific needs and expectations, ultimately leading to better project outcomes.
Develop communication plans: For each stakeholder, create a customized communication plan that outlines the frequency, format, and content of your interactions. Ensure that you are transparent, responsive, and consistent in your messaging, and that you address any concerns or feedback in a timely manner.
Establish feedback channels: Encourage open and honest feedback from stakeholders by providing accessible channels for them to voice their opinions, concerns, or suggestions. This can include regular meetings, surveys, or anonymous feedback forms. Make sure you listen to their input and adjust your approach accordingly.
Monitor and adapt: Continuously assess your engagement strategy’s effectiveness and make adjustments as needed. As your cybersecurity project progresses, new stakeholders may emerge, or existing stakeholders’ priorities may change. Regularly revisiting your engagement strategy will ensure you stay aligned with stakeholder needs and expectations.
When you’re ready, this is how we can help you#
MCSI understands the significance of Stakeholder Analysis in the cybersecurity field and aims to empower students to master this skill. By incorporating real-world scenarios in our cybersecurity exercises, we encourage students to identify various stakeholders, such as decision-makers, influencers, and implementers. This hands-on approach allows them to understand the roles and interests of different parties involved in a cybersecurity project.
Additionally, MCSI emphasizes the importance of clear and effective communication with stakeholders. Our exercises teach students how to convey their findings, recommendations, and progress updates to various stakeholders, keeping their needs, wants, and constraints in mind. By honing these skills, students become well-rounded cybersecurity professionals, ready to collaborate with diverse teams and contribute to successful cybersecurity initiatives.
Free Introduction to Cybersecurity: Start with our free course if you are new to our method.
Industry Certifications: Browse our catalogue of professional certifications to advance your career.

